Follow this advice to block malicious Office files from doing harm to your network even if you’ve implemented Microsoft’s recommended actions.
Once again attackers have used Office files in targeted attacks against Microsoft users. This time they used the Windows Explorer preview pane to deliver malicious .doc, .docm, and .docx files. Researchers have found that malicious .rtf files can also be used in such attacks. For this exploit, an attacker crafts a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine.
The attacker must convince a user to open the malicious document. So, your first line of defense is an educated user who doesn’t blindly open unexpected files. In addition, Microsoft Defender Antivirus and Microsoft Defender for Endpoint both provide detection and protections for the known vulnerability. Your antivirus tools may already include detections for this exploit as well.
Microsoft has released CVE-2021-40444 to track this vulnerability. Even when it’s fixed, don’t let your guard down. Instead, I recommend you keep one key protection that probably many of us are not doing to protect ourselves from malicious Office files including those used in this most current exploit.
Microsoft Defender Attack Surface Reduction rules
A vulnerability analyst at the CERT/CC, Will Dorman, pointed out that using Microsoft Defender’s Attack Surface Reduction (ASR) rules is a better long-term way to protect against such attacks. You can do this in multiple ways.
You can use Group Policy to configure ASR rules. This setting has been available since version 1709 of Windows 10. The exploit starts with an ActiveX CAB to place a DLL at a known location on the targeted system. A .CPL URI is then used to run that code. Microsoft’s mitigation focuses on blocking the ActiveX file so it can’t be called into action. Using ASR rules protects you not only for the current exploit but for future similar exploits.
To enable this setting, select in order:
- “Computer Configuration”
- “Administrative Templates”
- “Windows Components”
- “Microsoft Defender Antivirus”
- “Microsoft Defender Exploit Guard”
- “Attack Surface Reduction”
- «Configure Attack Surface Reduction rules» and make sure the value is set to «Enabled”
In earlier versions “Microsoft Defender antivirus” was called “Windows Defender antivirus.” so your group policy may need refreshing to track the new name even though the old name will still work.
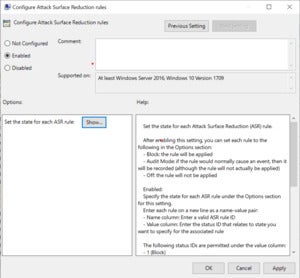
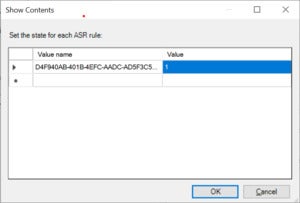
Select “Show…” and verify the rule ID in the “Value name” column and the desired state in the “Value” column is set as follows:
Value name: D4F940AB-401B-4EFC-AADC-AD5F3C50688A
Value: 1
ASR functions are available in Windows 10 Pro v1709 or later, Windows 10 Enterprise v1709 or later, Windows Server v1803 (Semi-Annual Channel) or later, and Windows Server 2019 or later. All ASR protections are available in Windows 10 Professional, but more reporting and monitoring functions are available in Enterprise SKUs.
If you prefer a more targeted protection and follow just the Microsoft-specific guidance, you can do so by disabling the installation of all ActiveX controls in Internet Explorer. You can do this for all sites by configuring a group policy using your local Group Policy editor or by updating the registry. In Group Policy, navigate in this order to:
- “Computer Configuration”
- “Administrative Templates”
- “Windows Components”
- “Internet Explorer”
- “Internet Control Panel”
- “Security Page”
Select each zone (Internet Zone, Intranet Zone, Local Machine Zone, or Trusted Sites Zone) and double-click on “Download signed ActiveX controls and Enable the policy”. Then set the option in the policy to “Disable”. Double-click on “Download unsigned ActiveX controls and Enable the policy”. Then set the option in the policy to “Disable”.
Microsoft recommends setting this for Internet Zone, Intranet Zone, Local Machine Zone, and Trusted Sites Zone. If you rely on ActiveX for any internal functions, this will allow previously installed and deployed ActiveX controls to still function but will block any new ActiveX controls from being installed and used in your systems. In my testing, I have not seen any side effects with disabling ActiveX in this manner. Alternatively, you can use registry keys to disable these ActiveX controls.
Disable Windows Explorer preview pane
It’s recommended to also disable shell preview in Windows Explorer. I do not enable preview pane in Windows Explorer unless I have a specific need or task in mind. It slows my computer down if it’s enabled.
To disable both the ActiveX and the Windows Explorer view of .doc, .docm, .docx and .rtf files, use the following registry key (also downloadable from this link):
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0]"1001"=dword:00000003"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1]"1001"=dword:00000003"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2]"1001"=dword:00000003"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3]"1001"=dword:00000003"1004"=dword:00000003
[-HKEY_CLASSES_ROOT\.docx\ShellEx\{8895b1c6-b41f-4c1c-a562-0d564250836f}]
[-HKEY_CLASSES_ROOT\.doc\ShellEx\{8895b1c6-b41f-4c1c-a562-0d564250836f}]
[-HKEY_CLASSES_ROOT\.docm\ShellEx\{8895b1c6-b41f-4c1c-a562-0d564250836f}]
[-HKEY_CLASSES_ROOT\.rtf\ShellEx\{8895b1c6-b41f-4c1c-a562-0d564250836f}]
The use of “-“ in front of these registry keys indicate that the registry file will remove these entries from your systems. If you wish to undo these settings, you can use this registry script to reenable.
Once Microsoft has patched for this issue, you may wonder if you are impacted by disabling the preview pane function. Many already either don’t enable the preview pane in Outlook or automatically block Word files from being previewed until you click on the enable content feature. Especially in an organization where you know you are targeted, you may wish to leave these protection settings in place even after any Microsoft patch is deployed.
Bottom line: Analyze your risk posture. Are you likely to be targeted? Do your users use preview pane in Windows Explorer? Do you have users who are a bit click happy? Do you have users that run with administrative rights? If the answer to all these risk questions is yes, then it’s wiser to use ASR rules and keep them in place even after this zero-day vulnerability is patched.

